Investigating the Grandbase Hack - a Walkthrough
The Grandbase hack, which resulted in the theft of $1.7 million, is a perfect example of how hackers exploit vulnerabilities in smart contracts to manipulate token minting and transfers. This section breaks down the key events leading to the hack and provides a deeper understanding of how such incidents occur in the blockchain space.
The Grandbase Hack Explained
The Grandbase hack took place when the private key of the contract deployer was compromised, allowing the hacker to access the core functionalities of the platform. Specifically, the attacker gained control over the minting function of the smart contract, which allowed them to create an unauthorized amount of 32.5 million GB tokens. These newly minted tokens were then swiftly transferred to the attacker’s wallet and exchanged for Ether (ETH).
To carry out this exploit, the hacker took advantage of the security vulnerabilities related to the centralized control of the minting function. In most decentralized platforms, the minting function is restricted to the contract owner, but in this case, the hacker's access to the deployer’s private key gave them full control of this critical function.
The hacker’s manipulation caused a significant inflation in the token supply, crashing the value of GB tokens and devastating the platform’s liquidity pools. As a result, Grandbase users were left with worthless tokens, and the platform’s reputation took a major hit. On-chain analysis shows that the attacker laundered the stolen funds by swapping the GB tokens for Ether and then transferring the assets through multiple wallets to obfuscate the trail.
This hack exposed the dangers of centralized control over key smart contract functions and underscored the importance of rigorous security audits and practices in DeFi platforms.
Viewing the Hack Through a Blockchain scanner
Grandbase Deployer Contract Background Research
Let’s start by going using the blockchain scanner Basescan.org. Basescan.org allows you to explore and search the Base Network for transactions, addresses, tokens, prices and other activities taking place on the blockchain.
Bear in mind that Grandbase is a Decentralized Finance (Defi) Protocol on the Base Network blockchain, which is why we need a blockchain viewer for Base.
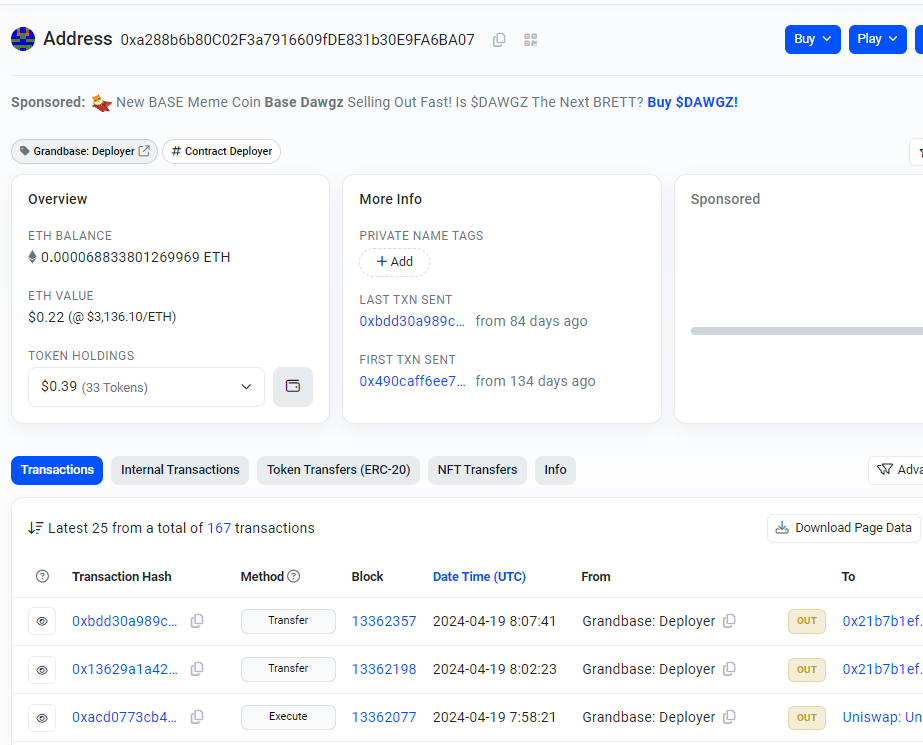
We use Basescan here to look at the address page for the Grandbase Deployer 0xa288b6b80C02F3a7916609fDE831b30E9FA6BA07
(https://basescan.org/address/0xa288b6b80C02F3a7916609fDE831b30E9FA6BA07)
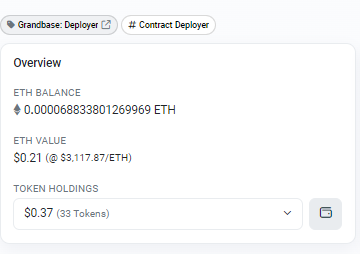
At first glance we see that the contract currently is identified as a Contract Deployer and that it is the Grandbase Deployer.
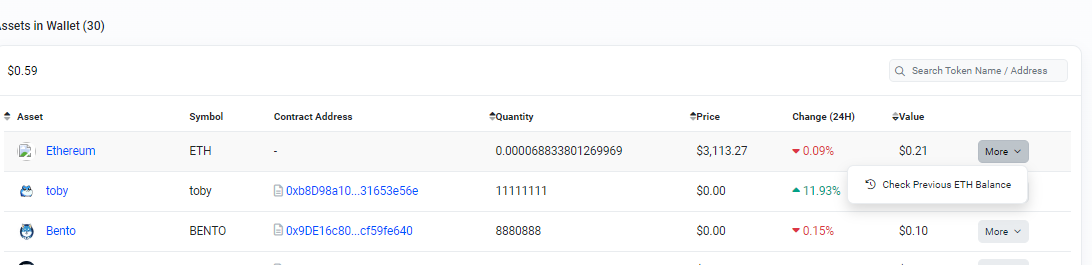
Also it shows that the contract currently has very little funds ($0.21 worth of ETH and Token Holdings that are also worth only $0.37).
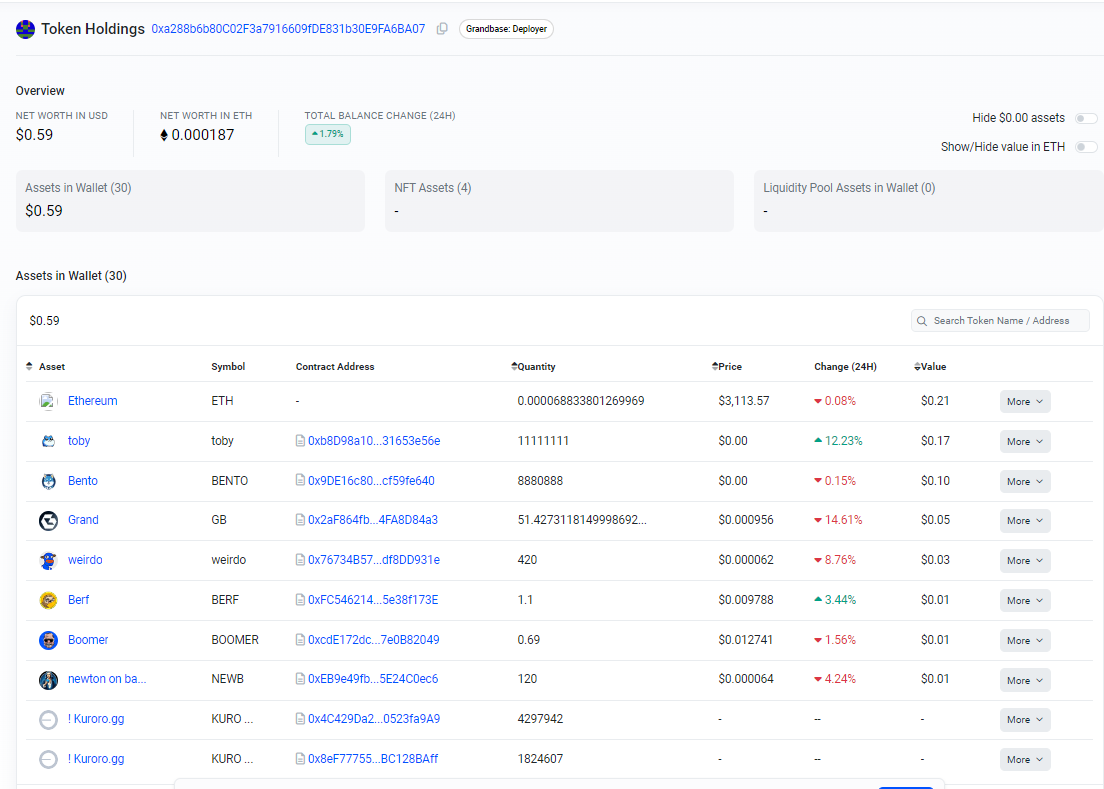
If we click on the wallet symbol it brings up to a page showing details on the contract’s tokens and
(https://basescan.org/tokenholdings?a=0xa288b6b80C02F3a7916609fDE831b30E9FA6BA07)
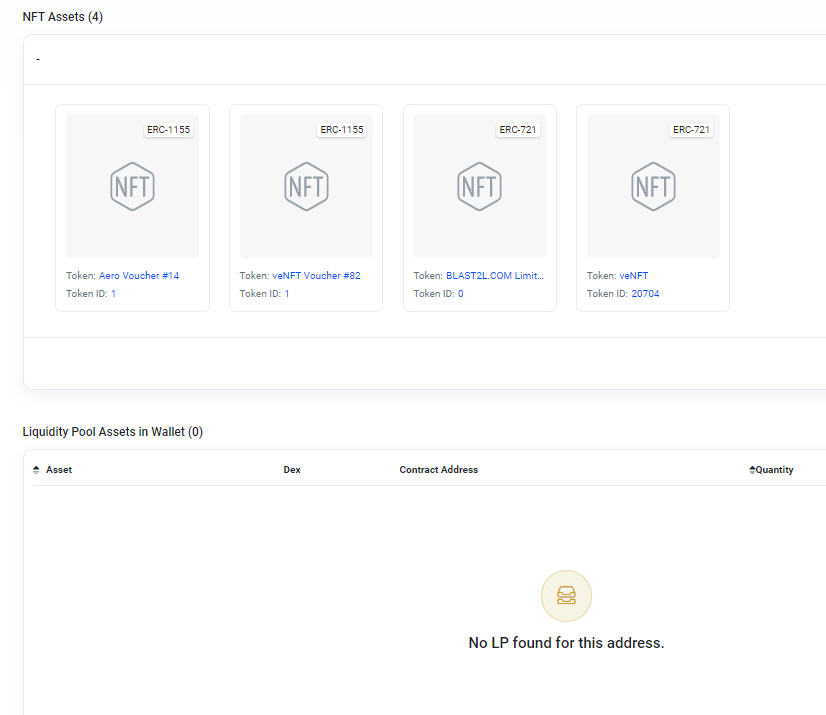
Further down the page we see the NFT and Liquidity Pool holdings that are also worthless
To view Contract Deployer’s past activities, we use the dropdown menu on the right of each token listing and it offers to check the wallet’s previous token balance.
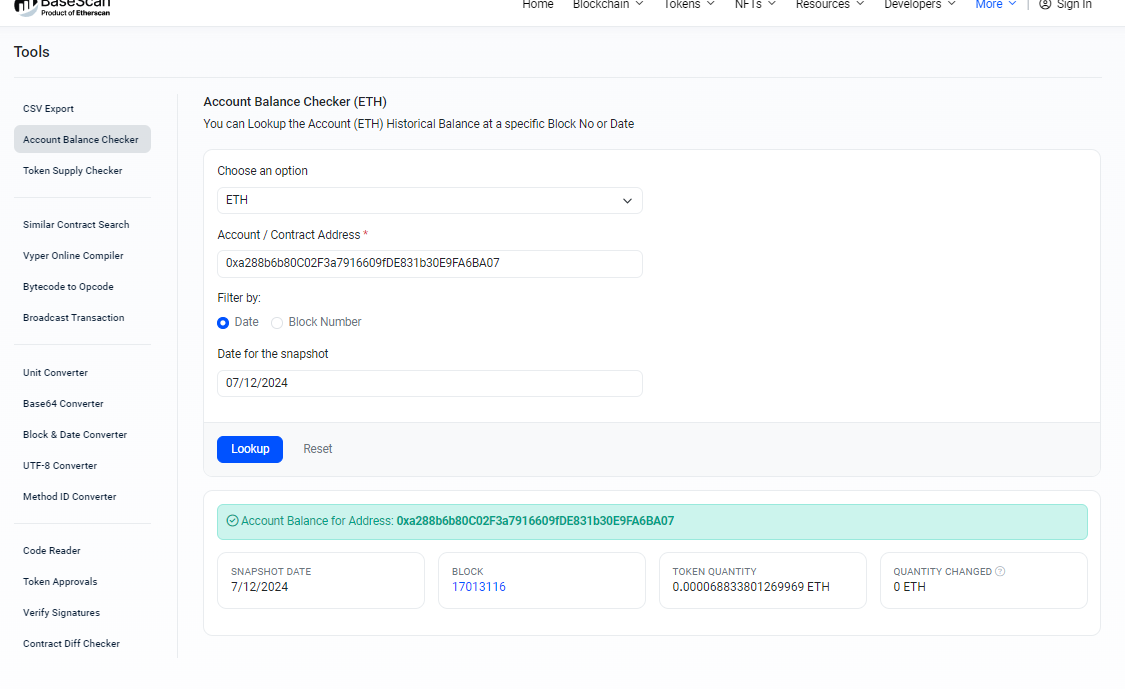
Depending on whether you chose a cryptocurrency or a token, clicking on this dropdown option will bring you to the Tools page where there is an Account Balance Checker and Token Supply Checker.
Because I clicked on Ethereum, we have the Account Balance Checker with the input data filled in (see the dropdown menus for address and type of currency to research).
Now this tool lets you choose any date and lookup how the address’s currency or tokens at that time.
In this case I searched Ethereum holdings on April 9, and the contract also did not have any EtH at that time.
Returning to the Grandbase: Deployer’s address page, we see that it has not been active in the previous 84 days.
It is clear that this Contract Deployer has gone dormant.
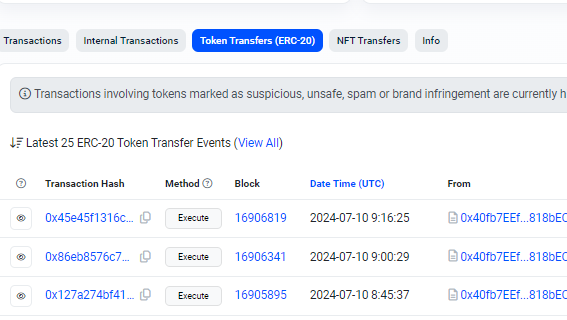
However, we do see more recent activity if we click on the tabs for NFT Transfers and Token Transfers (ERC-20). These would be worth further research if we wanted to understand what the organization has been up to lately.
We can also research the contract by looking at its first transactions.
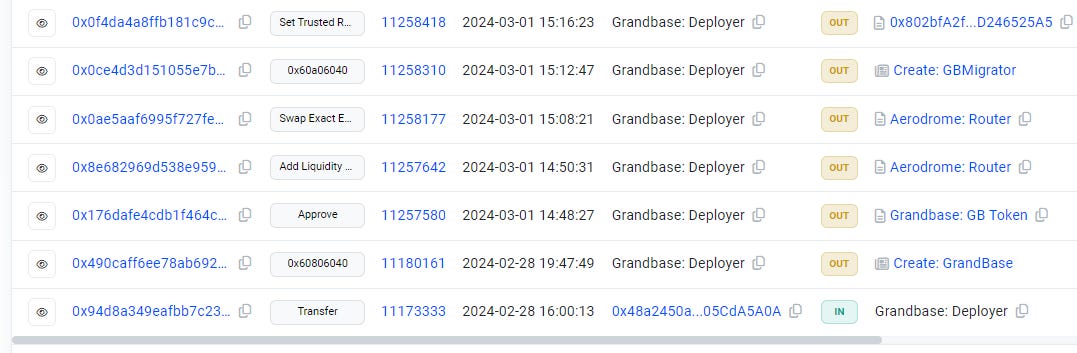
If we scroll all the way down to see the first transactions of the Grandbase: Deployer, we see on February 28, 2024 the deployer contract was created.
In the second transaction 3 hours later (second listing from the bottom), Grandbase: Deployer
0xa288b6b80C02F3a7916609fDE831b30E9FA6BA07
created the Grandbase: GB Token contract 0x2af864fb54b55900cd58d19c7102d9e4fa8d84a3
and initially created 17,500,000 GB Tokens (worth $47,106.85)
Viewing the First Transactions of the Hack
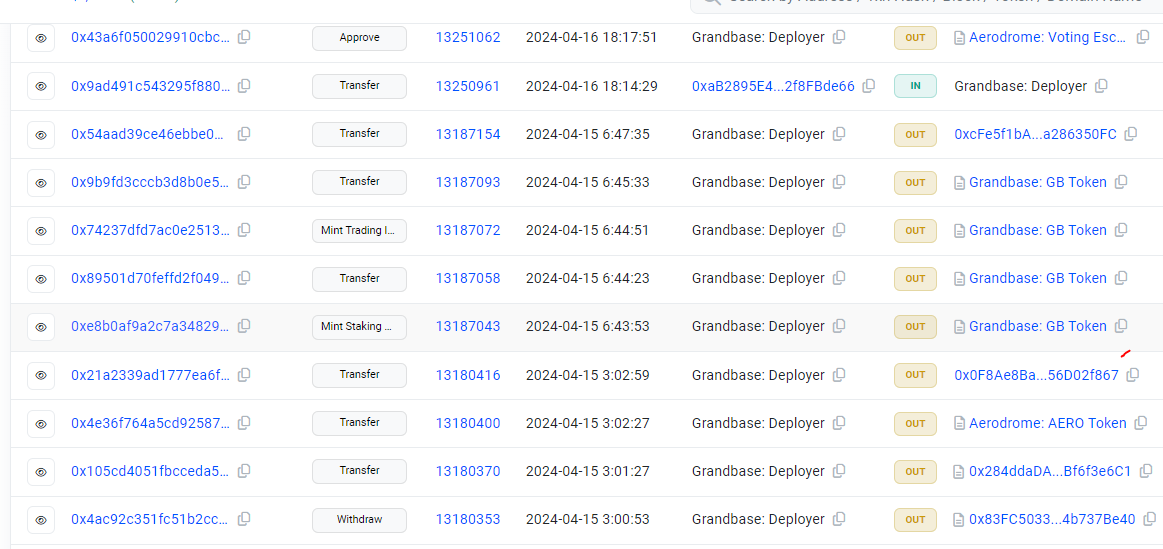
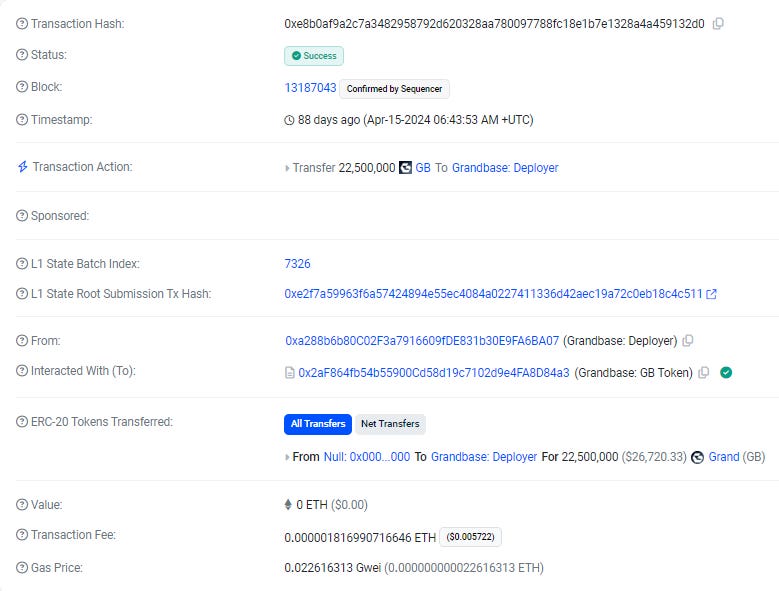
The beginning of the hack, and the first sign of exploiters gaining control of GB Deployer, first appeared in a transaction on the blockchain at 2024-04-15 6:43:53 UTC when 0xe8b0af9a2c7a3482958792d620328aa780097788fc18e1b7e1328a4a459132d0
mint 22,500,000 GB tokens,
(https://basescan.org/txs?a=0xa288b6b80C02F3a7916609fDE831b30E9FA6BA07&p=1)
(https://basescan.org/tx/0xe8b0af9a2c7a3482958792d620328aa780097788fc18e1b7e1328a4a459132d0)
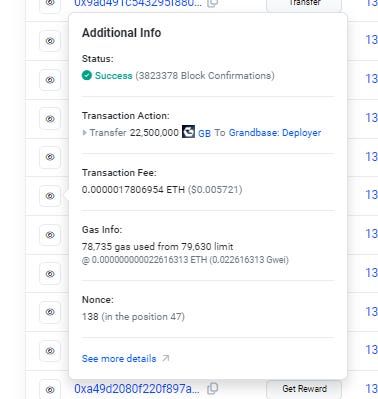
If we click on the transaction ID we see this depiction with transaction details.
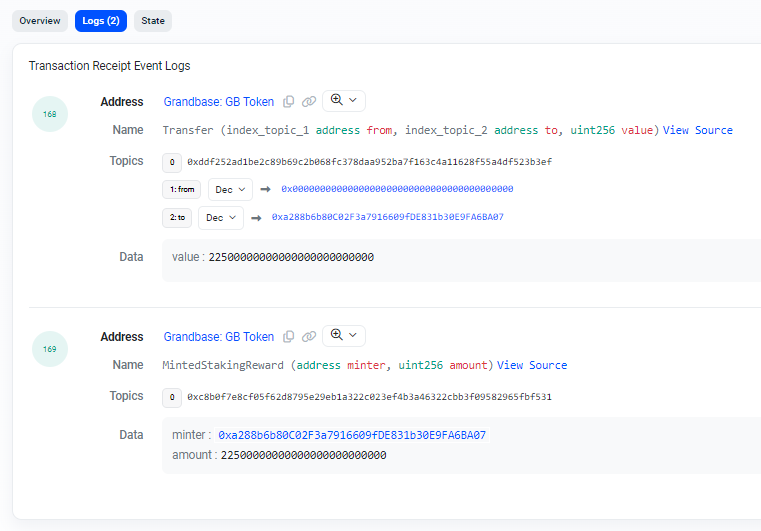
If we choose to look at the Logs tab, it gives us more specifics.
And after all of that, let's note that you could have just clicked on the eye symbol to pull up a summary of the transaction.
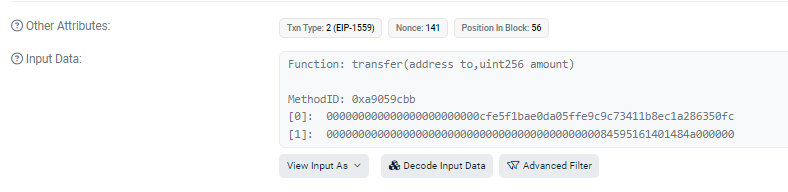
In the next transaction, after making/minting the tokens, it immediately Transfers 22,500,000 GB
To 0xcFe5f1bAe0DA05FFE9c9C73411b8Ec1a286350FC
(https://basescan.org/tx/0x89501d70feffd2f0492f393fabb2b261d0efdbd3e8f615be0c77deb3deeb41bf)
And the hackers repeat this with activity with another bunch of tokens.
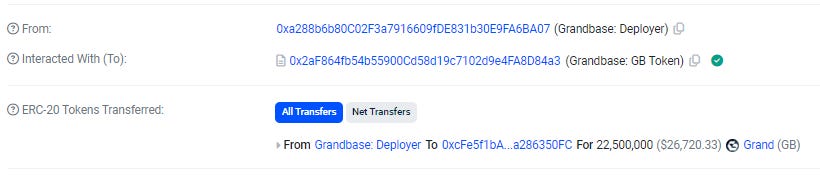
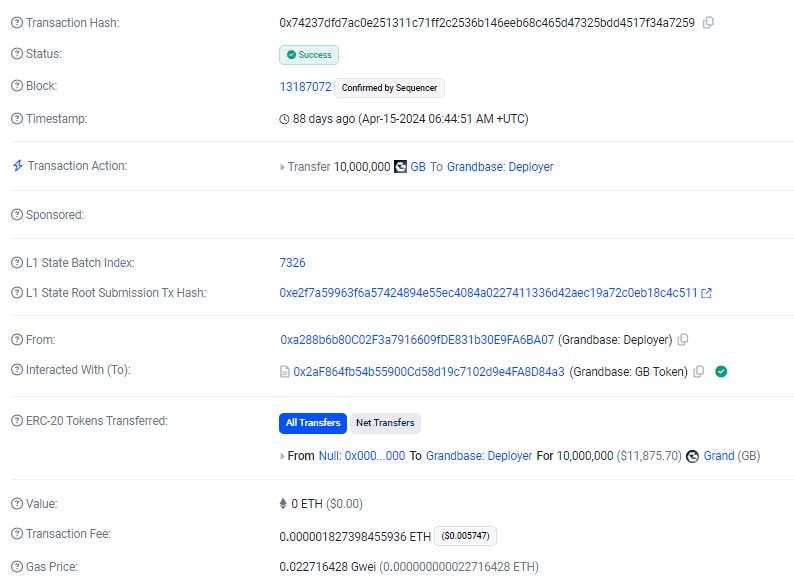
See below the full details of this transaction below to show you how it appears in the transactions details page. The hacker is stealing 10 million tokens in this case.
First the hacker mints 10,000,000 tokens and once again the details page describes it as a transfer of tokens to the Grandbase Deployer wallet.
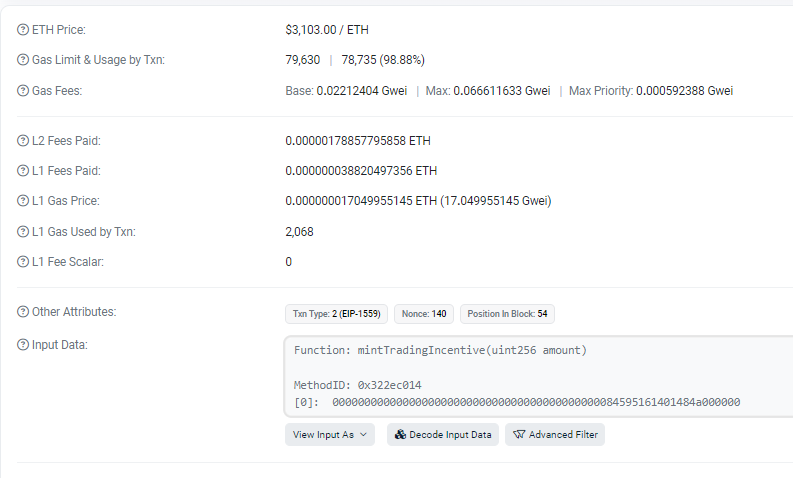
We see the input data includes the function call minting tokens.
In the next transaction the hacker transfers the tokens again to their own wallet.
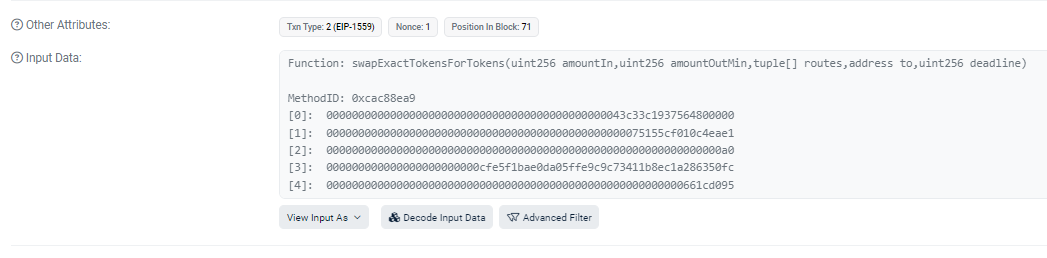
Swapping Tokens
The hacker’s address 50FC quickly began swapping Tokens for Wrapped Ether
In the transaction details page you see the “transaction action” listed as “Swap 20,000 GB for 8.494455323522291509 WETH on Aerodrome”
The phrase “Swap 20,000 GB for 8.494455323522291509 WETH on Aerodrome” refers to a cryptocurrency trade happening on a decentralized exchange, Aerodrome. In this case, 20,000 tokens of something called GB are being exchanged for about 8.49 WETH.
WETH stands for Wrapped Ether, which is basically Ether (ETH) in a form that’s compatible with Ethereum’s ERC-20 standard, making it easier to interact with other tokens and dApps.
So, essentially, you’re trading 20,000 GB tokens for a little over 8.49 WETH on the Aerodrome platform, which is likely a decentralized exchange that facilitates these peer-to-peer trades. The actual value of this swap depends on the market price of GB and WETH at the time of the transaction.
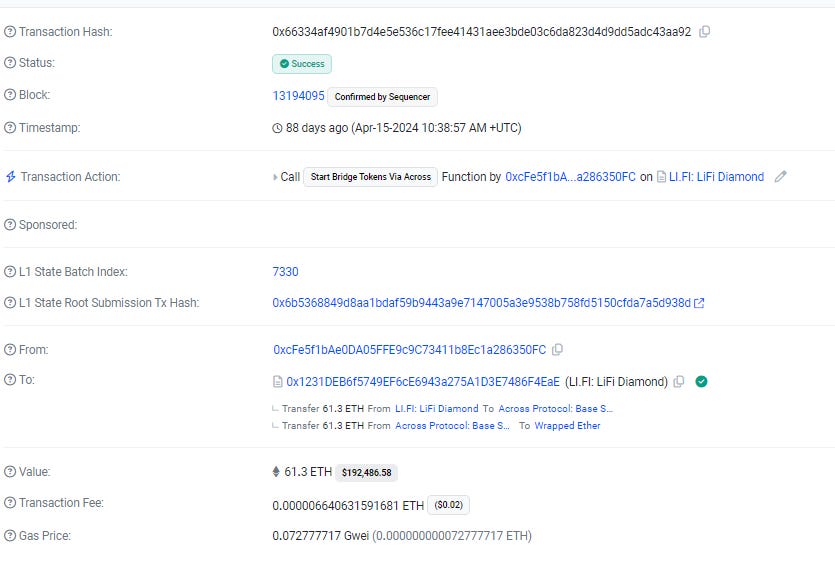
Bridging Tokens to Ethereum
The same hacker wallet later bridged tokens from Base to Ethereum
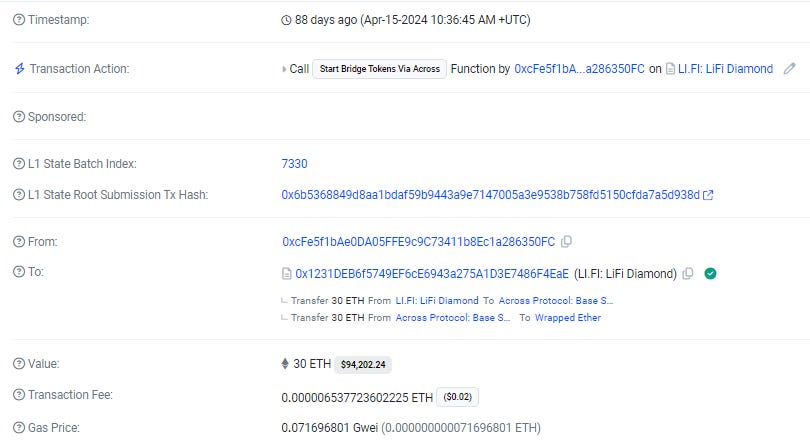
In the next transaction the hacker bridges more tokens
Final Transactions
The hacker continues to try to obfuscate their path by sending funds to multiple addresses and eventually starts to send them all back to one address.
Finally the movement of funds putters to a stop. The funds are transferred from several addresses to one, which forwards the money to another and then one more.
With all eyes on the wallet, the stolen funds have stayed in the last wallet unmoved.
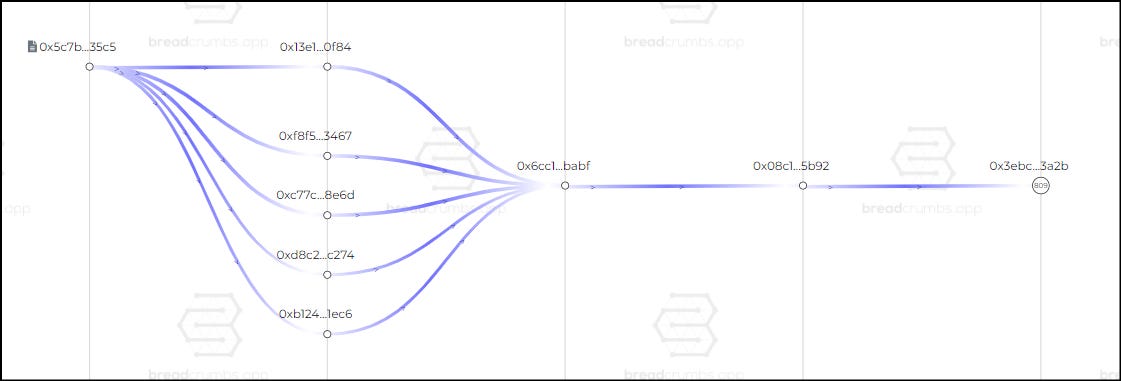
See the final path of the funds that are still sitting idle in the wallet.
For several transactions like this, Breadcrumbs.app is a good tool for visualizing the path of funds. See the final steps of the trail of stolen money below.
The final transaction occurred on April 23rd, 2024, when the address
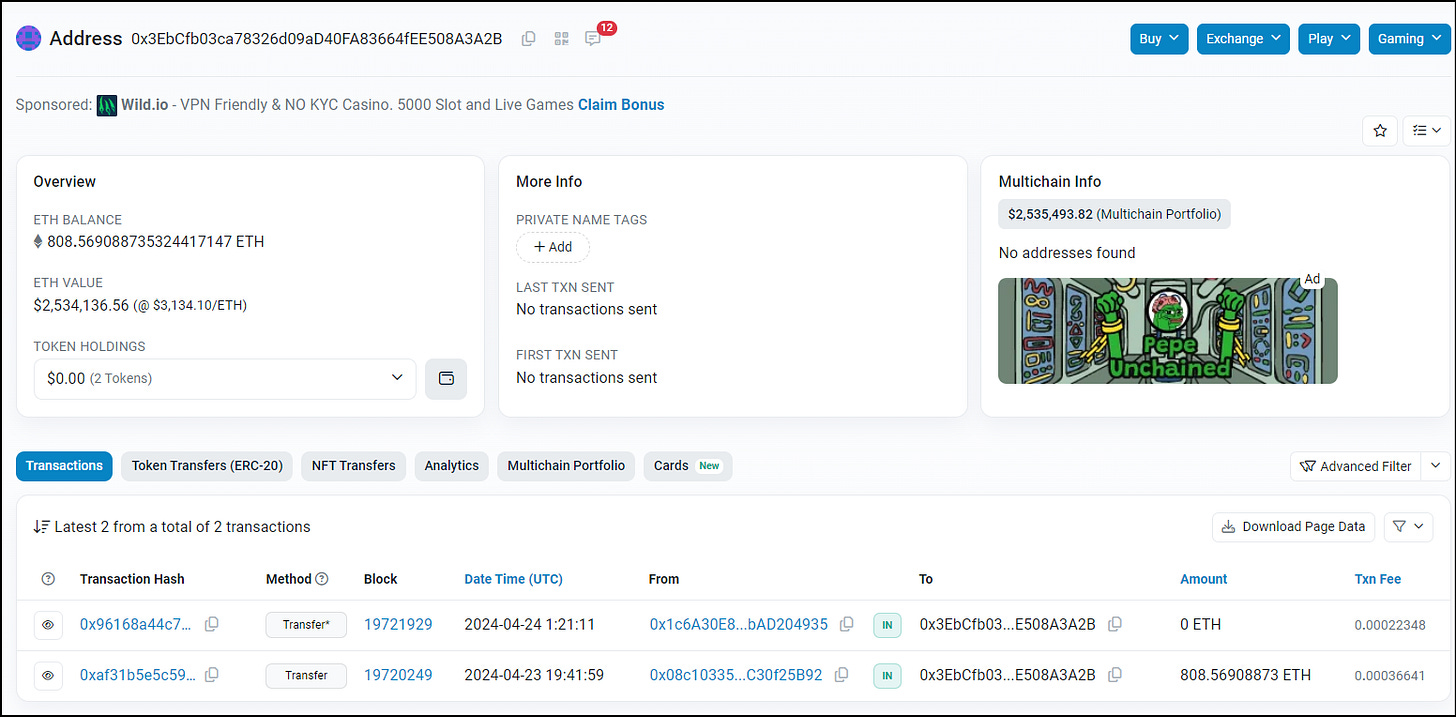
0x08c103353618E4333a3a949323b7217C30f25B92 sent approximately 808 ETH to 0x3EbCfb03ca78326d09aD40FA83664fEE508A3A2B.
From there, the funds appear to be lying dormant sitting at the last address.
This may be yet another case where the stolen funds can’t be retrieved by hackers.
Communication From the Victim to the Public and the Hackers
Before wrapping things up, let’s address another important factor occuring in parallel to the hack, communication from the victim.
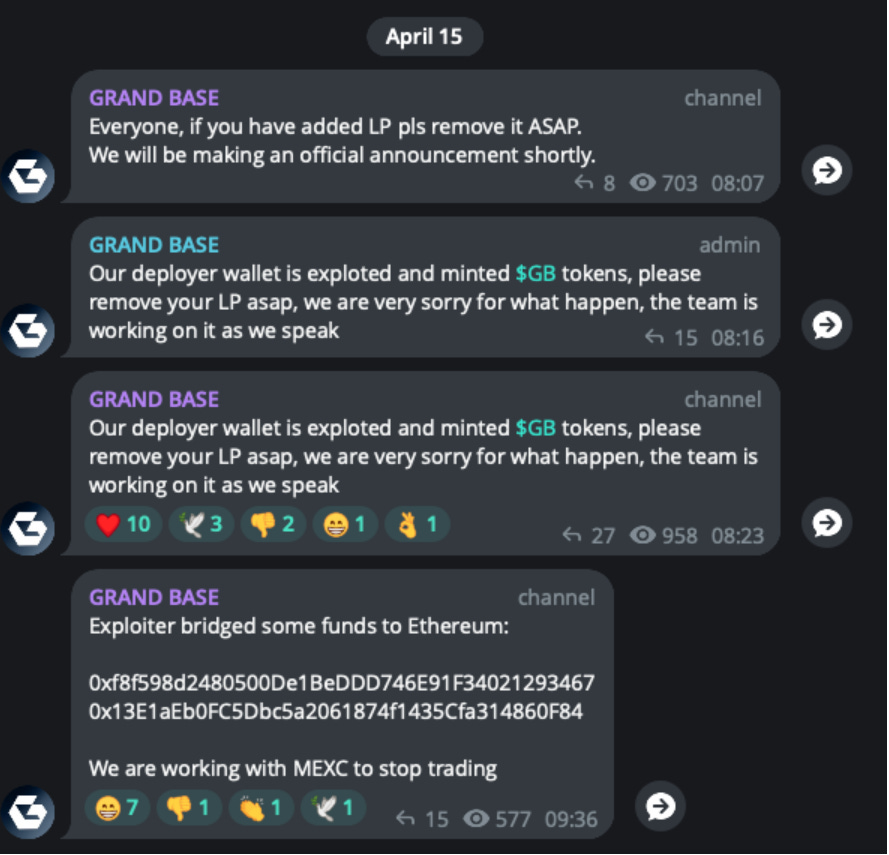
A surprising amount of communication and statements to the public in this area happens on Telegram. A message on the Grandbase Telegram Channel announced on the day of the hack:
"Our deployer wallet is exploited and minted $GB tokens, please remove your LP asap, we are very sorry for what happen, the team is working on it as we speak"
(https://t.me/grandbase_fi/15354)
The use of telegram also reflects how company statements are not always in more conventional media sources.
If a Telegram channel is open, like this one, you can view the channel by clicking "preview" or use the URL with the added "/s/" in the middle of the URL (https://t.me/s/reflectrfl)
Similarly if you are looking at a webpage for just one specific statement posted to the channel (https://t.me/reflectrfl/62) - there should be a "context" button at the bottom that will bring you to the location of the statement within the channel conversation. But you can also add the "s" into the URL as before (https://t.me/s/reflectrfl/62)
Note that in both cases the number 62 at the end of the URL reflects the specific post.
Communication via Crypto Transaction
Grandbase leadership used a crypto transaction to communicate with the hackers.
This is a phenomenon of blockchains that will be addressed in the following section, but first there is an interesting postscript to the story.
Communication via Transaction
As noted, the last address appears to be just holding on to the money since then. However, if we view the address in Basescan.org we see one more transaction.
As you can see in the transaction logs above, the address received the 808 ETH on April 23rd. Then, about 5 hours later there is a second transaction, this one is from (0x1c6A30E8fc66cBBd122b20272D2786CbAD204935) (4935).
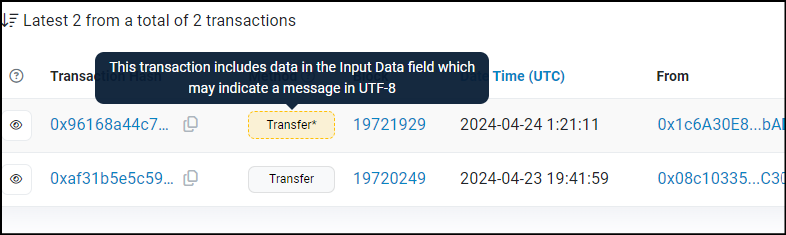
The Method "Transfer" includes a star and if we hover the cursor over it, we get this pop up message saying that the Input Data Field of the transaction has data that could be a message in UTF-8. (UTF-8 is a character encoding system for electronic communication)
By clicking on the transaction hash to get the transaction details page, we see that the transaction action lists a message.
(https://etherscan.io/tx/0x96168a44c74036b858aad002647dda55db375c86e0ba1d2da1c6c52d9cc35d5f)
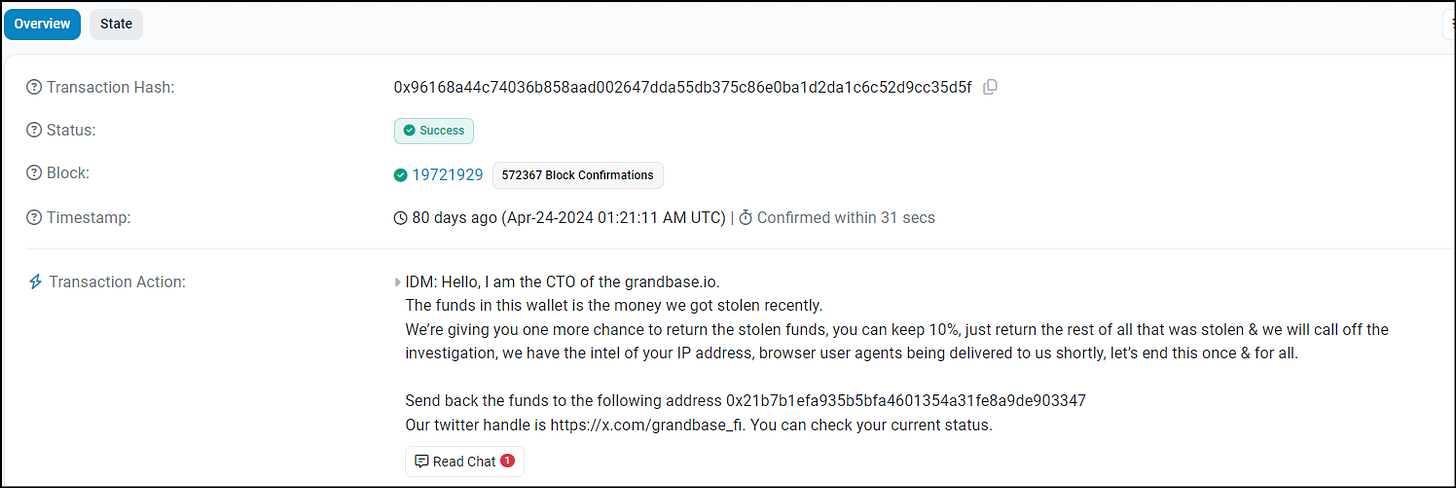
"IDM:
Hello, I am the CTO of the grandbase.io.
The funds in this wallet is the money we got stolen recently.
We’re giving you one more chance to return the stolen funds, you can keep 10%, just return the rest of all that was stolen & we will call off the investigation, we have the intel of your IP address, browser user agents being delivered to us shortly, let’s end this once & for all.
Send back the funds to the following address 0x21b7b1efa935b5bfa4601354a31fe8a9de903347
Our twitter handle is https://x.com/grandbase_fi. You can check your current status."
(https://etherscan.io/tx/0x96168a44c74036b858aad002647dda55db375c86e0ba1d2da1c6c52d9cc35d5f)
Here is a chance to understand these kinds of messages and how to find them in your investigations.
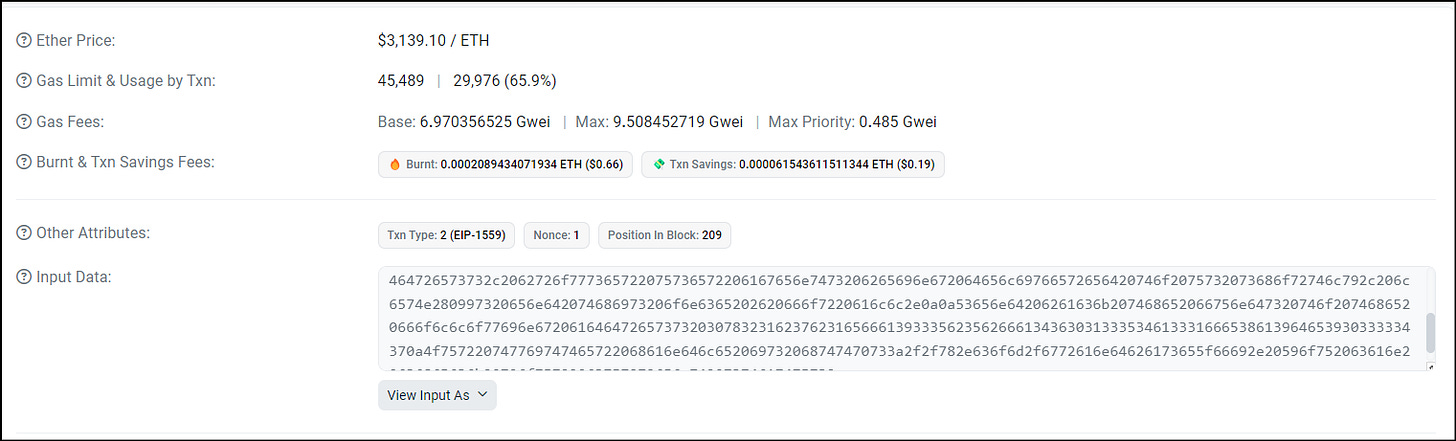
We already have the message, but just to walk through the motions, we could check the input field. Scroll down to the "Input Data" field and see what is printed in the field. Note that the transfer alert said that the message was in UTF-8
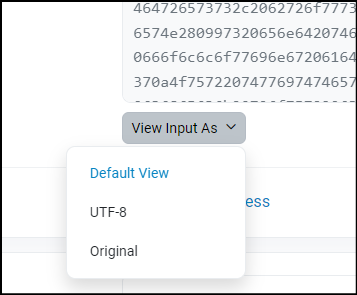
So click on the dropdown where it says "View Input As" and select UTF-8
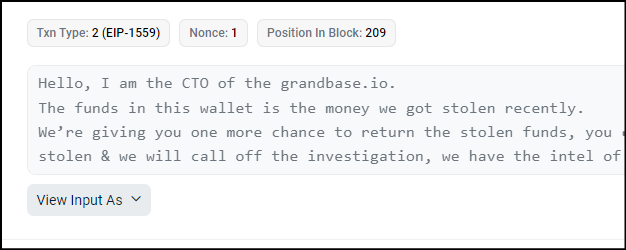
Now the data is changed in the field is the message we saw above
Here we see that the data is sent with the transaction, where we usually see function calls with transaction details, instead it is a message.
If we had not known better, this would have just looked like a transfer of 0 ETH. Now let's return to the phenomenon of stolen funds sitting idle in public view.
The Grandbase hack sheds light on critical vulnerabilities in decentralized finance (DeFi), providing key insights into how private key compromises can lead to widespread damage. By analyzing this attack, we understand how hackers can exploit centralized control over smart contract functions—such as minting and transferring tokens—once they gain access to a deployer wallet's private key.
By delving into the technical breakdown of the hack, we can see how investigators trace and analyze such incidents, giving us a blueprint for understanding similar attacks in the future.